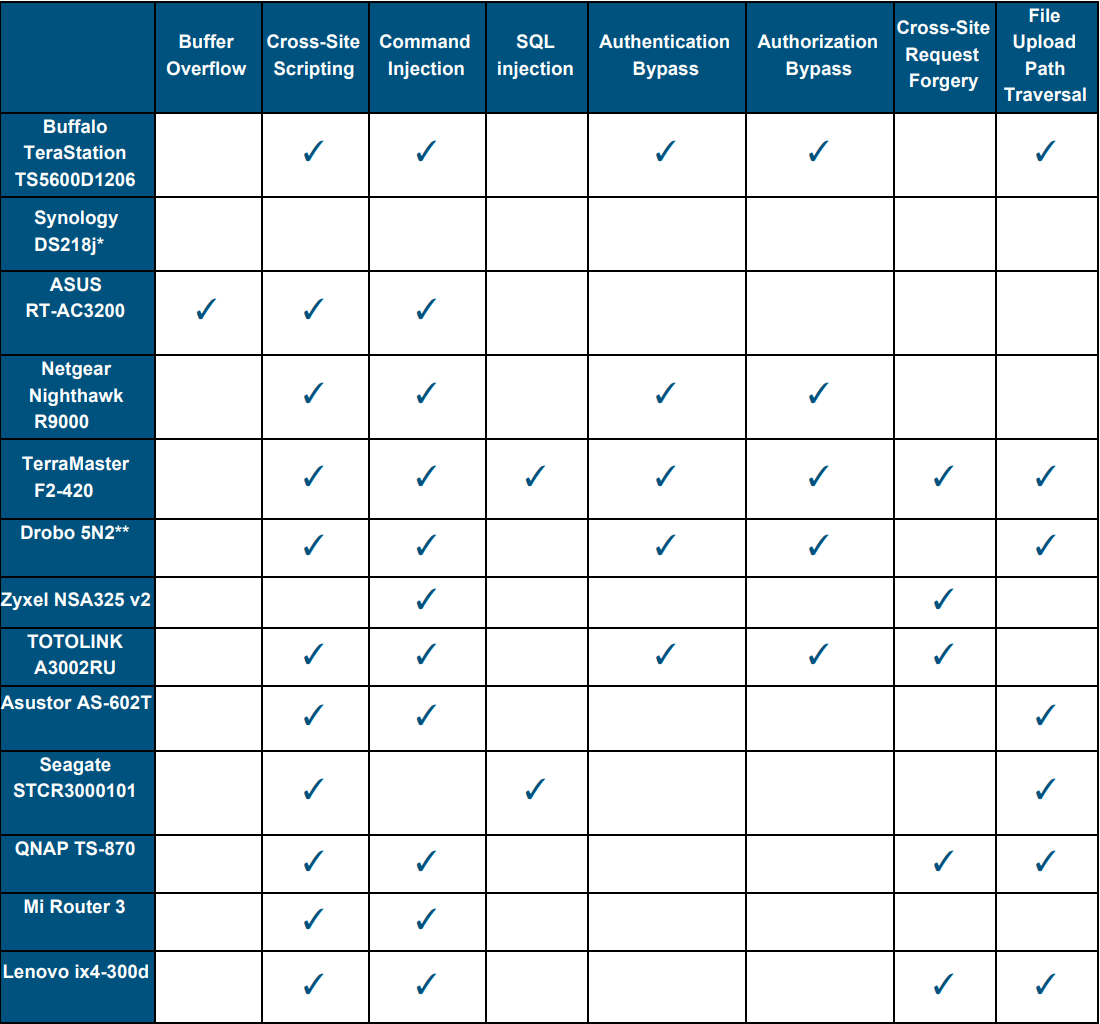
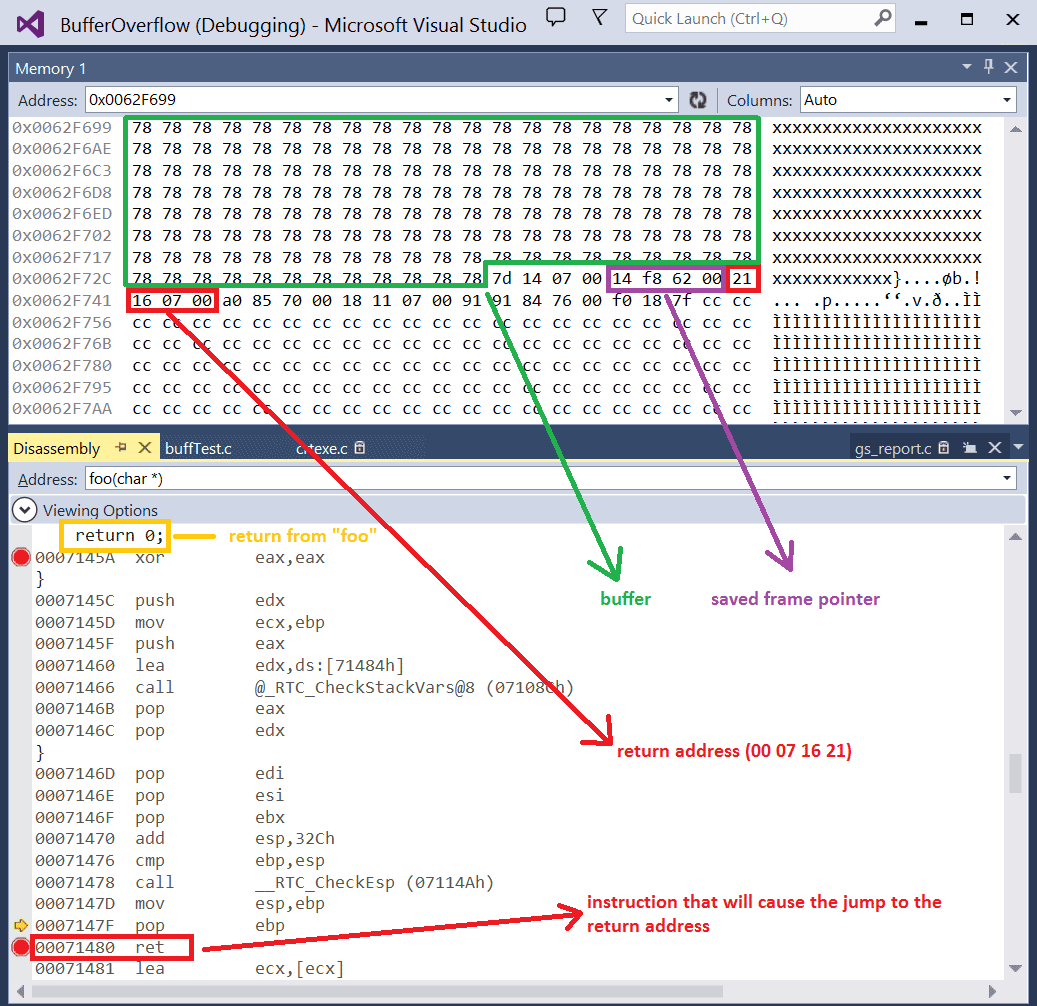
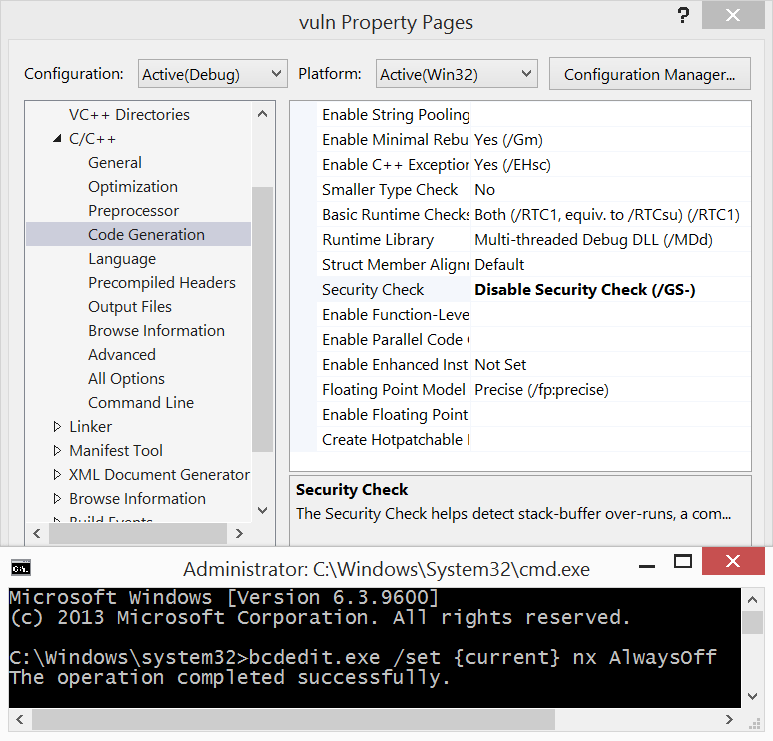
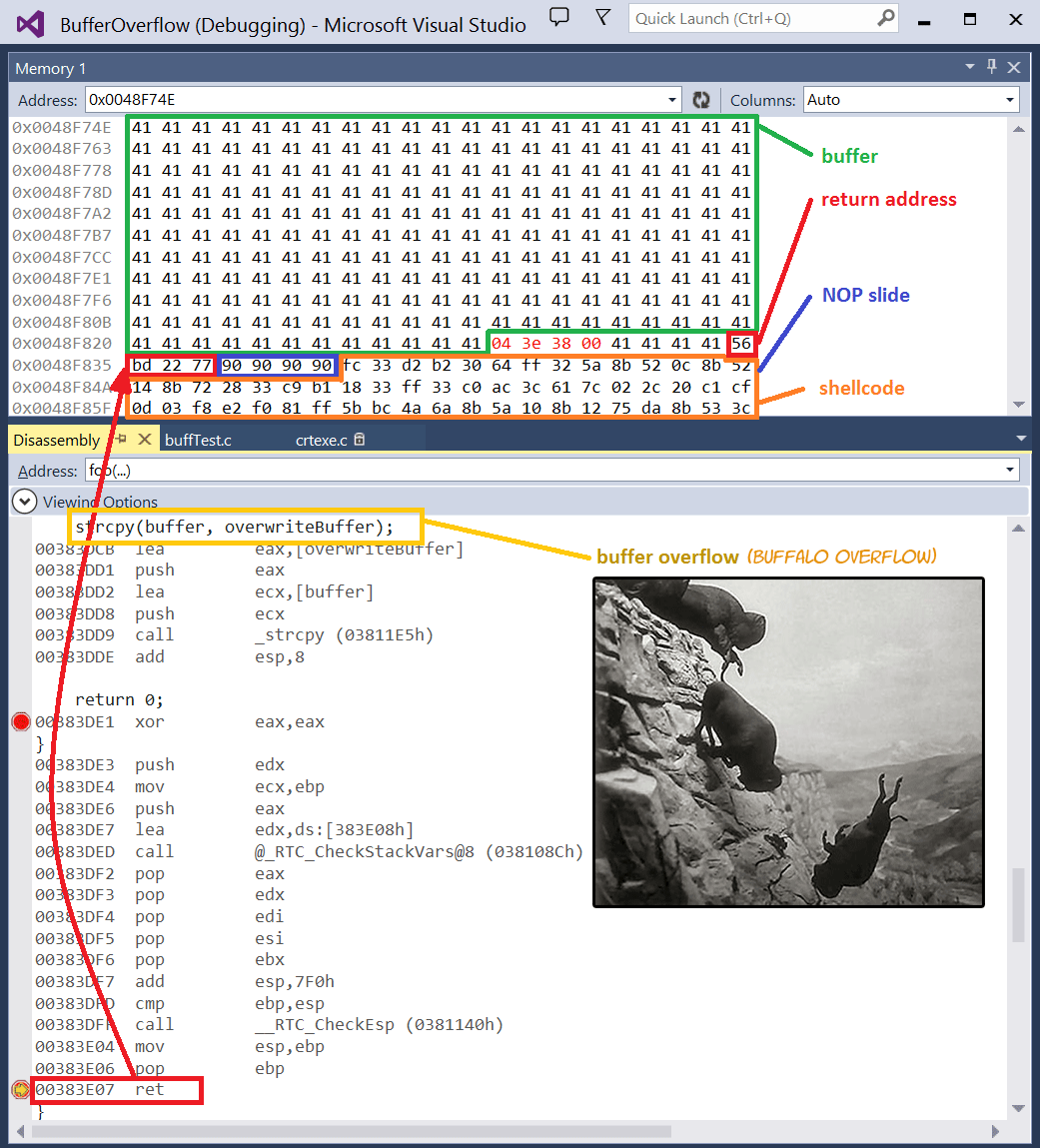
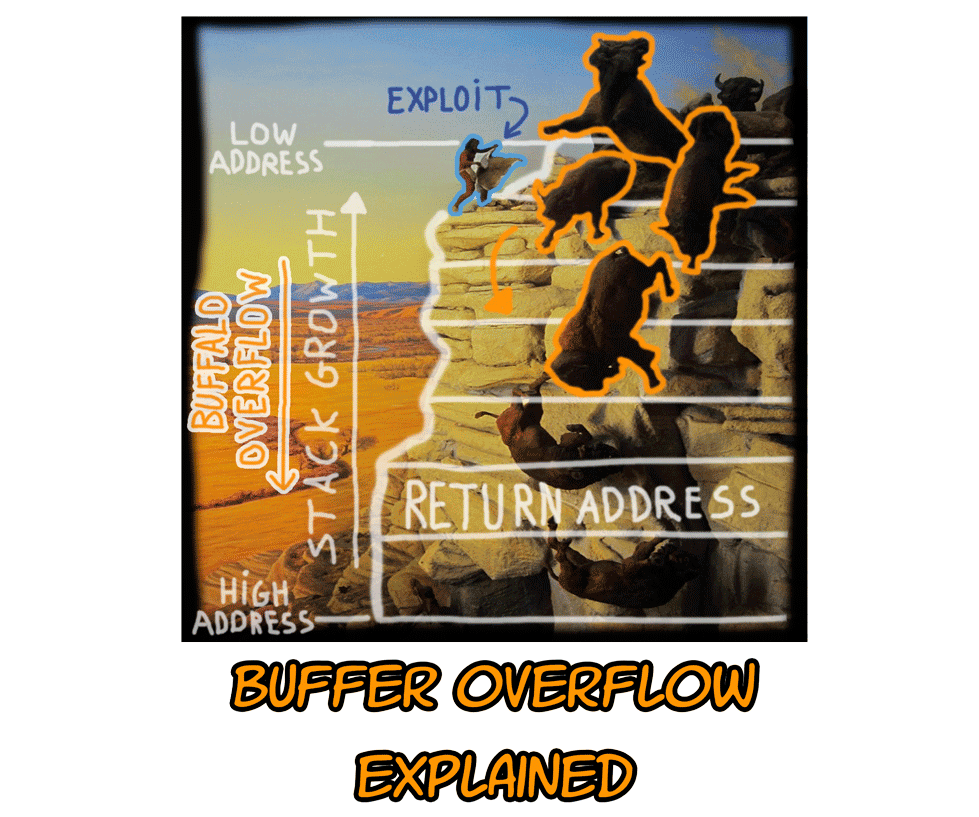
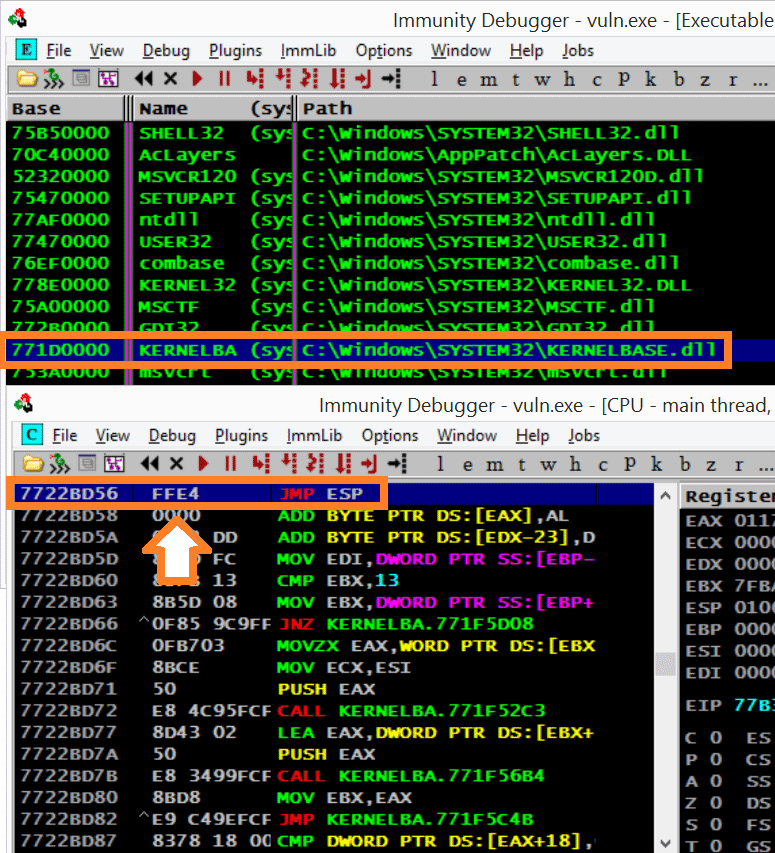
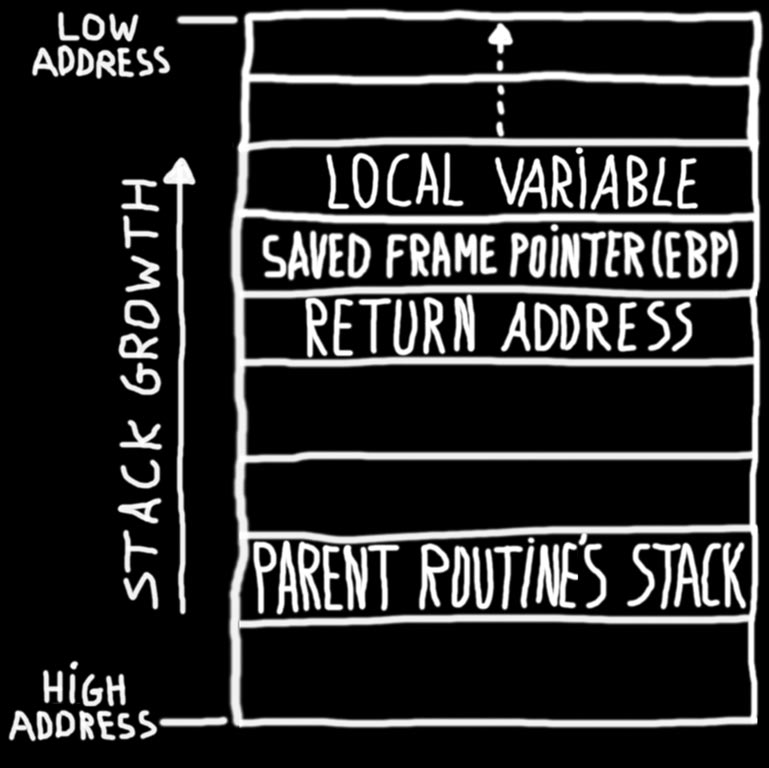
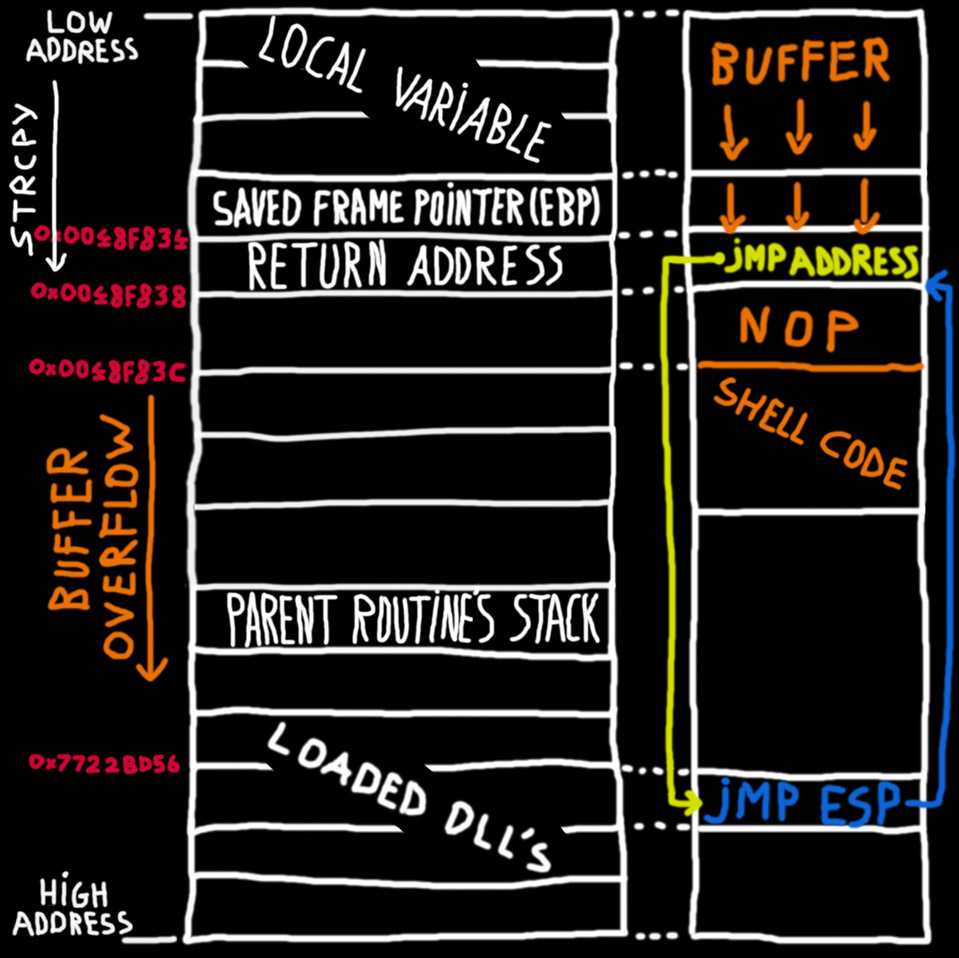
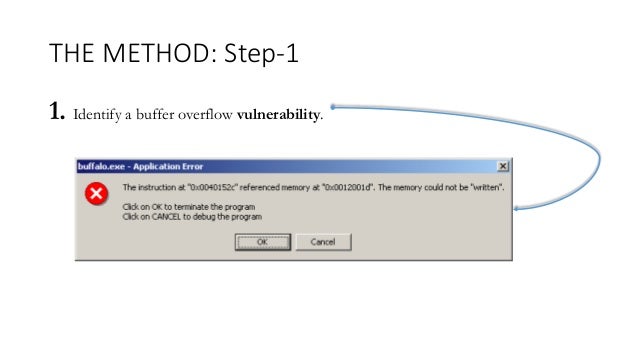
An introduction to computer buffer overflow problem on using unsecured C or C++ standard functions in C programs
![Motorcycle Passenger Tossed Around Like Ragdoll in Buffalo Attack in South Dakota [Video] | lovebscott.com Motorcycle Passenger Tossed Around Like Ragdoll in Buffalo Attack in South Dakota [Video] | lovebscott.com](https://www.lovebscott.com/wp-content/uploads/2020/08/7b64f4334f4b428bb3d09c22a99be882_md-1280x720.jpg)
Motorcycle Passenger Tossed Around Like Ragdoll in Buffalo Attack in South Dakota [Video] | lovebscott.com

An introduction to computer buffer overflow problem on using unsecured C or C++ standard functions in C programs

Matthew Hall on Twitter: "Also... not really “full stack” if memory corruption vulns aren't considered at all... some may say “yeah but when was the last time you found a buffer overflow